Photo from wikipedia
Software-defined networking (SDN) is the key outcome of extensive research efforts over the past few decades toward transforming the Internet to a more programmable, configurable, and manageable infrastructure. At the… Click to show full abstract
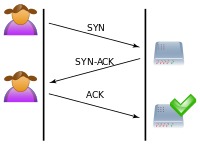
Software-defined networking (SDN) is the key outcome of extensive research efforts over the past few decades toward transforming the Internet to a more programmable, configurable, and manageable infrastructure. At the same time, SDN will surely become a new target of cyber attackers. In this paper, we point out one of the critical vulnerabilities in SDNs, the capacity of controller, which is most likely to be attacked. Due to the logical centralized management, the breakdown of a controller may disrupt a whole SDN network, which can be easily occurred by Packet-In messages flooding attack (a network-level DDoS attack). To provide a robust environment in SDN, we propose an effective detection method, which has low overhead and high accuracy. We first classify the potential switches that are compromised using Bayesian Network, which is a supervised learning algorithm. Then, we deploy the anomaly detection on the vulnerable switches to detect the Packet-In messages flooding attack based on fuzzy c-means. Extensive simulations and testbed-based experiments show that the proposed solution can defeat the Packet-In messages flooding attack with low overhead and high accuracy.
Journal Title: Soft Computing
Year Published: 2018
Link to full text (if available)
Share on Social Media: Sign Up to like & get
recommendations!