
Contaminated disposable rubber gloves as evidence samples after a chemical attack with nerve agents.
Sign Up to like & getrecommendations! Published in 2023 at "Drug testing and analysis"
DOI: 10.1002/dta.3468
Abstract: Nerve agents have been used recently in the Syrian civil war. Collecting relevant samples for retrospective identification of an attack is often problematic. The article deals with the possibility of using of contaminated gloves as… read more here.
Keywords: disposable rubber; identification; evidence; attack ... See more keywords

Network security situation assessment with network attack behavior classification
Sign Up to like & getrecommendations! Published in 2022 at "International Journal of Intelligent Systems"
DOI: 10.1002/int.22867
Abstract: To solve the problems that existing network security situation assessment (NSSA) methods are difficult to extract features and have poor timeliness, an NSSA method with network attack behavior classification (NABC) is proposed. First, an NABC… read more here.
Keywords: network; network attack; attack behavior; situation ... See more keywords

Knowledge graph and behavior portrait of intelligent attack against path planning
Sign Up to like & getrecommendations! Published in 2022 at "International Journal of Intelligent Systems"
DOI: 10.1002/int.22874
Abstract: The broad application of artificial intelligence (AI) shows more and more vulnerabilities. Adversaries have more opportunities to attack AI systems. For example, unmanned vehicles may be interfered with by adversaries in path planning, resulting in… read more here.
Keywords: unmanned vehicles; technology; attack; path planning ... See more keywords

An intelligent proactive defense against the client‐side DNS cache poisoning attack via self‐checking deep reinforcement learning
Sign Up to like & getrecommendations! Published in 2022 at "International Journal of Intelligent Systems"
DOI: 10.1002/int.22934
Abstract: A new class of poisoning attacks has recently emerged targeting the client‐side Domain Name System (DNS) cache. It allows users to visit fake websites unconsciously, thereby revealing their information, such as passwords. However, the current… read more here.
Keywords: proactive defense; deep reinforcement; client side; defense ... See more keywords

Posttraumatic stress disorder in the short and medium term following the World Trade Center attack among Asian Americans.
Sign Up to like & getrecommendations! Published in 2018 at "Journal of community psychology"
DOI: 10.1002/jcop.22092
Abstract: This study investigated patterns of probable posttraumatic stress disorder (PTSD) and their predictors among 2,431 Asian American and 31,455 non-Hispanic White World Trade Center (WTC) Registry participants 2-3 years and 5-6 years after the WTC… read more here.
Keywords: attack; stress disorder; posttraumatic stress; world trade ... See more keywords

A case of panic attack developing after THC-O acetate inhalation using an e-cigarette device.
Sign Up to like & getrecommendations! Published in 2023 at "Neuropsychopharmacology reports"
DOI: 10.1002/npr2.12345
Abstract: AIM Tetrahydrocannabinol acetate (THC-O) is a cannabinoid-based product, and few medical studies have evaluated the effects of THC-O on humans. Recently, e-cigarettes have become popular among teenagers and young adults worldwide. However, there have been… read more here.
Keywords: cigarette; attack; case; device ... See more keywords

Cube Attacks on Non-Blackbox Polynomials Based on Division Property
Sign Up to like & getrecommendations! Published in 2018 at "IEEE Transactions on Computers"
DOI: 10.1007/978-3-319-63697-9_9
Abstract: The cube attack is a powerful cryptanalytic technique and is especially powerful against stream ciphers. Since we need to analyze the complicated structure of a stream cipher in the cube attack, the cube attack basically… read more here.
Keywords: attack; blackbox; attacks non; cube attack ... See more keywords

The DizzyQuest: to have or not to have… a vertigo attack?
Sign Up to like & getrecommendations! Published in 2020 at "Journal of Neurology"
DOI: 10.1007/s00415-020-10043-x
Abstract: The DizzyQuest, an app-based vestibular diary, provides the opportunity to capture the number and nature of vertigo attacks in daily life. To accomplish this, the DizzyQuest provides different strategies: event sampling using an attack questionnaire,… read more here.
Keywords: attack; vertigo attacks; questionnaire; vertigo attack ... See more keywords
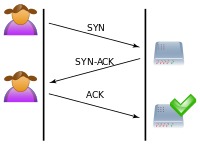
Defending against Packet-In messages flooding attack under SDN context
Sign Up to like & getrecommendations! Published in 2018 at "Soft Computing"
DOI: 10.1007/s00500-018-3407-3
Abstract: Software-defined networking (SDN) is the key outcome of extensive research efforts over the past few decades toward transforming the Internet to a more programmable, configurable, and manageable infrastructure. At the same time, SDN will surely… read more here.
Keywords: attack; messages flooding; packet messages; flooding attack ... See more keywords

Non-deterministic approach to allay replay attack on iris biometric
Sign Up to like & getrecommendations! Published in 2018 at "Pattern Analysis and Applications"
DOI: 10.1007/s10044-018-0681-8
Abstract: Biometric-based verification system has emerged as a powerful authentication tool. Despite its advantages over traditional systems, it is prone to several attacks. These attacks may creep through the biometric system and may prove fatal if… read more here.
Keywords: attack; replay attack; system; non deterministic ... See more keywords

Differential audio analysis: a new side-channel attack on PIN pads
Sign Up to like & getrecommendations! Published in 2018 at "International Journal of Information Security"
DOI: 10.1007/s10207-018-0403-7
Abstract: This paper introduces a low-cost side-channel attack that identifies the pressed key of tamper-proof mechanical keypads by exploiting the sound that emanates from the pressed key. Classical sound-based attacks usually identify the pressed key using… read more here.
Keywords: attack; pin pads; side channel; channel attack ... See more keywords