
Hardware-Impaired PHY Secret Key Generation With Man-in-the-Middle Adversaries
Sign Up to like & getrecommendations! Published in 2022 at "IEEE Wireless Communications Letters"
DOI: 10.1109/lwc.2022.3147952
Abstract: In this letter, we examine the PHY layer secret key generation (PHY-SKG) scheme in the presence of man-in-the-middle (MiM) adversary, while legitimate parties suffer from hardware impairments (HIs). Different from previous works on PHY-SKG that… read more here.
Keywords: man middle; key generation; secret key; phy ... See more keywords
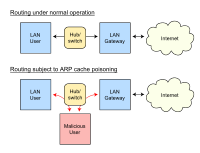
A Formal Verification of ArpON – A Tool for Avoiding Man-in-the-Middle Attacks in Ethernet Networks
Sign Up to like & getrecommendations! Published in 2022 at "IEEE Transactions on Dependable and Secure Computing"
DOI: 10.1109/tdsc.2021.3118448
Abstract: Since the nineties, the Man-in-The-Middle (MITM) attack has been one of the most effective strategies adopted for compromising information security in network environments. In this article, we focus our attention on ARP cache poisoning, which… read more here.
Keywords: arp cache; cache poisoning; man middle; attacks ethernet ... See more keywords

Detecting man-in-the-middle attacks via hybrid quantumclassical protocol in software-defined network
Sign Up to like & getrecommendations! Published in 2023 at "Indonesian Journal of Electrical Engineering and Computer Science"
DOI: 10.11591/ijeecs.v31.i1.pp205-211
Abstract: Man-in-the-middle (MitM) attacks became one of the most risk attacks on OpenFlow communication channel in software-defined networking, its detection is a very hard task due there is no authentication in OpenFlow protocol. This channel is… read more here.
Keywords: network; software defined; man middle; protocol ... See more keywords

Testbed for LoRaWAN Security: Design and Validation through Man-in-the-Middle Attacks Study
Sign Up to like & getrecommendations! Published in 2021 at "Applied Sciences"
DOI: 10.3390/app11167642
Abstract: The low-power wide-area (LPWA) technologies, which enable cost and energy-efficient wireless connectivity for massive deployments of autonomous machines, have enabled and boosted the development of many new Internet of things (IoT) applications; however, the security… read more here.
Keywords: validation; man middle; security; middle attacks ... See more keywords