
A Flexible KP-ABE Suit for Mobile User Realizing Decryption Outsourcing and Attribute Revocation
Sign Up to like & getrecommendations! Published in 2020 at "Wireless Personal Communications"
DOI: 10.1007/s11277-020-07503-y
Abstract: Attribute based encryption is an effective method which can solve the access control problem of cloud storage. Realizing both efficient attributes revocation and outsourcing decryption would enhance mobile user experience. In this paper, we present… read more here.
Keywords: system; decryption; flexible abe; mobile user ... See more keywords

Efficient user authentication protocol for distributed multimedia mobile cloud environment
Sign Up to like & getrecommendations! Published in 2020 at "Journal of Ambient Intelligence and Humanized Computing"
DOI: 10.1007/s12652-019-01467-z
Abstract: The rapid growth of smart-phone users, mobile services and mobile applications, poses the challenges of storage space, processing capability, and battery lifetime at the users smart phones. Mobile cloud computing helps to overcome these challenges.… read more here.
Keywords: authentication protocol; user authentication; protocol; mobile user ... See more keywords

State of the art on road traffic sensing and learning based on mobile user network log data
Sign Up to like & getrecommendations! Published in 2018 at "Neurocomputing"
DOI: 10.1016/j.neucom.2017.03.096
Abstract: Abstract With the improvement of the storage and big data processing technology, mobile operators are able to extract and store a large amount of mobile network generated user behavior data, in order to develop various… read more here.
Keywords: traffic; traffic sensing; network; log data ... See more keywords
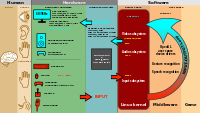
An Automated Model-Based Approach for Developing Mobile User Interfaces
Sign Up to like & getrecommendations! Published in 2021 at "IEEE Access"
DOI: 10.1109/access.2021.3066007
Abstract: The ever-increasing number of mobile platforms constitutes a challenge for application developers, who must develop efficient mobile applications for multiple platforms. Recently, a specific interest is being taken in the Model Based User Interface Development… read more here.
Keywords: approach; model based; user interfaces; mobile user ... See more keywords

Load Balanced Mobile User Recruitment for Mobile Crowdsensing Systems
Sign Up to like & getrecommendations! Published in 2017 at "IEEE Communications Letters"
DOI: 10.1109/lcomm.2017.2732403
Abstract: In this letter, we study the mobile user recruitment problem for mobile crowdsensing systems. Instead of minimizing the overall sensing cost or user utility, this letter aims to optimize the load balancing of the mobile… read more here.
Keywords: crowdsensing systems; mobile user; load balanced; mobile crowdsensing ... See more keywords

Novel Workload-Aware Approach to Mobile User Reallocation in Crowded Mobile Edge Computing Environment
Sign Up to like & getrecommendations! Published in 2022 at "IEEE Transactions on Intelligent Transportation Systems"
DOI: 10.1109/tits.2021.3086827
Abstract: A mobile edge computing (MEC) paradgim is evolving as an increasingly popular means for developing and deploying smart-city-oriented applications. MEC servers can receive a great deal of requests from devices of mobile users, especially in… read more here.
Keywords: mobile edge; user reallocation; aware approach; mobile user ... See more keywords

Location Privacy Protection via Delocalization in 5G Mobile Edge Computing Environment
Sign Up to like & getrecommendations! Published in 2023 at "IEEE Transactions on Services Computing"
DOI: 10.1109/tsc.2021.3112659
Abstract: In the past several years, we have witnessed a variety of mechanisms for protecting mobile users’ location privacy, e.g., k-anonymity, cloaking, encryption, etc. Unfortunately, existing techniques suffer from a common limitation - mobile users’ locations… read more here.
Keywords: mobile edge; privacy; mobile user; location privacy ... See more keywords
A Deep Transfer Learning Based Visual Complexity Evaluation Approach to Mobile User Interfaces
Sign Up to like & getrecommendations! Published in 2022 at "Traitement du Signal"
DOI: 10.18280/ts.390511
Abstract: Visual complexity is an important factor affecting the efficiency and functionality of user interfaces. Its impact on the user's impression and the usability is significant, especially for mobile applications with constraints such as layout size,… read more here.
Keywords: complexity evaluation; mobile user; user interfaces; visual complexity ... See more keywords