
Asymptotic security analysis of teleportation-based quantum cryptography
Sign Up to like & getrecommendations! Published in 2020 at "Quantum Information Processing"
DOI: 10.1007/s11128-020-02701-w
Abstract: We prove that the teleportation-based quantum cryptography protocol presented in Gordon and Rigolin (Opt Commun 283:184, 2010), which is built using only orthogonal states encoding the classical bits that are teleported from Alice to Bob,… read more here.
Keywords: based quantum; security analysis; security; quantum cryptography ... See more keywords

Quasi-cyclic multi-edge LDPC codes for long-distance quantum cryptography
Sign Up to like & getrecommendations! Published in 2018 at "npj Quantum Information"
DOI: 10.1038/s41534-018-0070-6
Abstract: The speed at which two remote parties can exchange secret keys in continuous-variable quantum key distribution (CV-QKD) is currently limited by the computational complexity of key reconciliation. Multi-dimensional reconciliation using multi-edge low-density parity-check (LDPC) codes… read more here.
Keywords: quantum; reconciliation; distance; quantum cryptography ... See more keywords

A Survey on Quantum Cryptography
Sign Up to like & getrecommendations! Published in 2018 at "Chinese Journal of Electronics"
DOI: 10.1049/cje.2018.01.017
Abstract: Quantum cryptography (QC) as an important technology to protect the security of the future network communication, has gained extensive attention from both academia and industry in recent years. This paper provides a concise up-to-date review… read more here.
Keywords: cryptography; quantum; survey quantum; quantum cryptography ... See more keywords

Implementation vulnerabilities in general quantum cryptography
Sign Up to like & getrecommendations! Published in 2018 at "New Journal of Physics"
DOI: 10.1088/1367-2630/aade06
Abstract: Quantum cryptography is information-theoretically secure owing to its solid basis in quantum mechanics. However, generally, initial implementations with practical imperfections might open loopholes, allowing an eavesdropper to compromise the security of a quantum cryptographic system.… read more here.
Keywords: quantum; implementation; quantum cryptography; security ... See more keywords

Quantum Cryptography-as-a-Service for Secure UAV Communication: Applications, Challenges, and Case Study
Sign Up to like & getrecommendations! Published in 2022 at "IEEE Access"
DOI: 10.1109/access.2021.3138753
Abstract: The sudden demand rises in security made researchers come up with solutions that provide instantaneous safety better than the state of the art solutions. The quest for securing data began in the Spartan era. People… read more here.
Keywords: quantum cryptography; quantum; case study;

A Flexible NTT-Based Multiplier for Post-Quantum Cryptography
Sign Up to like & getrecommendations! Published in 2023 at "IEEE Access"
DOI: 10.1109/access.2023.3234816
Abstract: In this work an NTT-based (Number Theoretic Transform) multiplier for code-based Post-Quantum Cryptography (PQC) is presented, supporting Quasi Cyclic Low/Moderate-Density Parity-Check (QC LDPC/MDPC) codes. The cyclic matrix product, which is the fundamental operation required in… read more here.
Keywords: post quantum; based multiplier; flexible ntt; ntt based ... See more keywords

Quantum cryptography needs a reboot: A failed security product could someday power large-scale quantum computing - [News]
Sign Up to like & getrecommendations! Published in 2019 at "IEEE Spectrum"
DOI: 10.1109/mspec.2019.8847578
Abstract: Quantum technologies are at the vanguard of many engineering fields today. Yet one of the earliest quantum applications still appears very far indeed from any kind of wide-spread, commercial rollout. read more here.
Keywords: reboot failed; quantum; failed security; cryptography needs ... See more keywords

Reliable Architectures for Composite-Field-Oriented Constructions of McEliece Post-Quantum Cryptography on FPGA
Sign Up to like & getrecommendations! Published in 2021 at "IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems"
DOI: 10.1109/tcad.2020.3019987
Abstract: Code-based cryptography based on binary Goppa codes is a promising solution for thwarting attacks based on quantum computers. The McEliece cryptosystem is a code-based public-key cryptosystem which is believed to be resistant against quantum attacks.… read more here.
Keywords: post quantum; cryptography; composite field; quantum cryptography ... See more keywords

Practical quantum cryptography
Sign Up to like & getrecommendations! Published in 2017 at "JETP Letters"
DOI: 10.1134/s0021364017090077
Abstract: A quantum cryptography system based on a 4-basis protocol with geometrically uniform states is tested in a series of experiments. Quantum states of light transmitted through real fiber optic communication channels to a distance of… read more here.
Keywords: practical quantum; quantum; quantum cryptography;
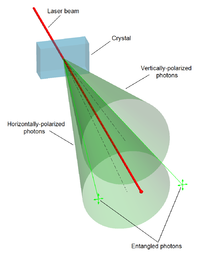
Quantum entanglement and composite keys in quantum cryptography
Sign Up to like & getrecommendations! Published in 2017 at "JETP Letters"
DOI: 10.1134/s0021364017120098
Abstract: The security of quantum cryptography protocols after a quantum key distribution (QKD) session is formulated in terms of proximity between two situations: quantum states corresponding to real and ideal situations after QKD. The measure of… read more here.
Keywords: entanglement composite; composite keys; quantum cryptography; security ... See more keywords

Mesoscopic quantum cryptography
Sign Up to like & getrecommendations! Published in 2017 at "Journal of Experimental and Theoretical Physics"
DOI: 10.1134/s1063776117020054
Abstract: Since a strictly single-photon source is not yet available, in quantum cryptography systems, one uses, as information quantum states, coherent radiation of a laser with an average number of photons of μ ≈ 0.1–0.5 in… read more here.
Keywords: quantum; line; quantum cryptography; average number ... See more keywords